🔍 Search
📥 Subscribe
ARP Spoofing Attack
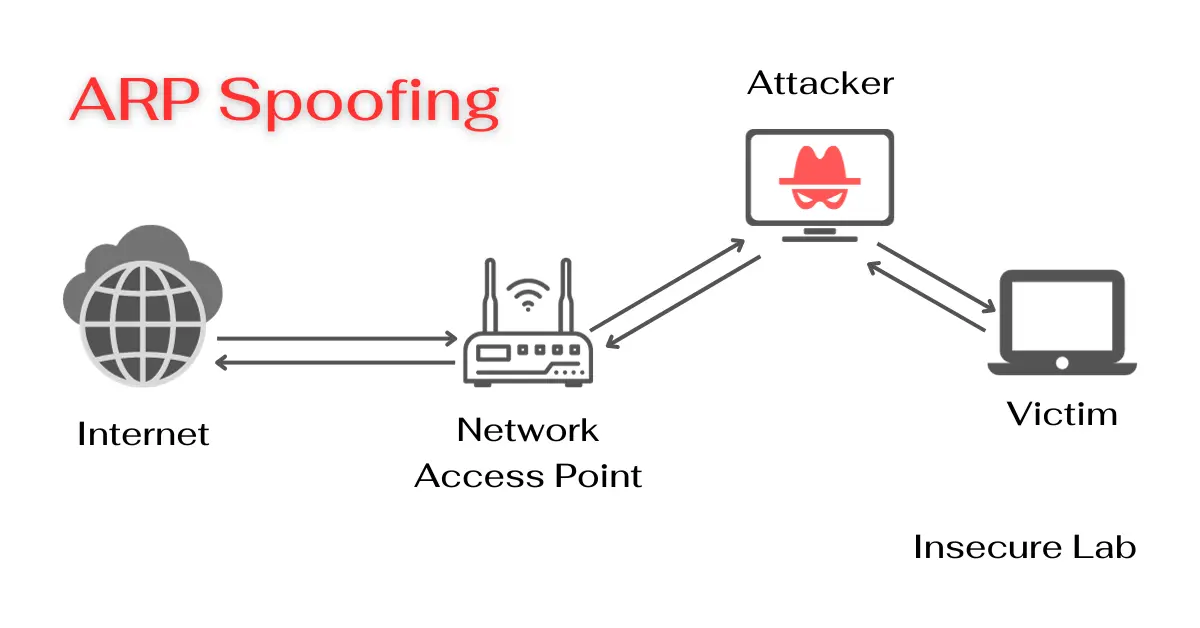
Table of Contents
This guide explains what is ARP spoofing and how it works in ethical hacking. It also explains how to detect and prevent arp spoofing attack in cyber security.
What is ARP Spoofing?
ARP spoofing or ARP poisoning is a cyber attack in which the attacker sends spoofed ARP messages on the LAN to associate their MAC address with the IP address of a legitimate device, such as a default gateway or server.
This is possible because ARP does not verify the identity of the sender, allowing devices to accept ARP responses without even a prior request. Once the attacker's MAC address is associated with the target's IP, they can intercept, modify, or block data intended for that IP, making a variety of malicious activities possible.
Understanding ARP
Address Resolution Protocol (ARP) is a communications protocol used in computer networking to map IP addresses to MAC addresses. In a local area network (LAN), when a device needs to send data to another, it uses ARP to find the MAC address associated with the target IP address.
This process involves broadcasting an ARP request to all devices on the network, and the device with the matching IP address responds with an ARP reply containing its MAC address.
This mapping is stored in an ARP cache for efficiency, but the protocol lacks authentication, making it vulnerable to attacks such as ARP spoofing.
Purpose of ARP Spoofing Attack
ARP spoofing attacks serve several malicious purposes, ranging from intercepting sensitive communications to disrupting network services. Some of the main purposes are given below:
1. Man-in-the-Middle (MITM) Attack
In a MITM attack, the attacker stands between two communicating devices, intercepting and potentially altering their messages without their knowledge. This is achieved by using ARP spoofing to reroute traffic through the attacker's machine, tricking both devices into sending data as if they were communicating directly.
2. Denial of Service (DoS) Attack
The purpose of a DoS attack is to disrupt normal network operations, making services unavailable to legitimate users. Through ARP spoofing, the attacker can send traffic to the wrong address or overload a device with excessive requests, causing a disruption in service.
3. Session Hijacking
Session hijacking involves the attacker gaining unauthorized access to a user's active session on a network service, such as logging into a website. By intercepting traffic via ARP spoofing, the attacker can capture session tokens or cookies, allowing them to impersonate the user.
How ARP Spoofing Works?
The attack process usually goes through the steps below:
- Network Access: The attacker often gains access to the target LAN via Wi-Fi or a wired connection, which requires a direct network presence.
- Target Identification: The attacker scans the network to identify the IP addresses of at least two devices, such as a workstation and a router, using tools such as a network scanner.
- Forged ARP Messages: The attacker, using tools such as Arpspoof or Driftnet, sends unsolicited ARP replies, claiming that their MAC address matches the IP address of the target device.
- Cache Poisoning: Target devices update their ARP caches with the attacker's MAC address, and accept the forged information as legitimate.
- Traffic Interception: All traffic between target devices is redirected through the attacker's device, making actions such as eavesdropping, data modification, or denial of service possible.
Detection Methods
- Check ARP Cache:
Display the ARP table using the '
arp -a' command in the administrator shell (Windows/Linux) and look for multiple IP addresses mapped to the same MAC address, which indicates an attack. - Monitor Network Traffic: Analyze network traffic for unusual patterns, such as unexpectedly high traffic on a single device, which indicates traffic redirection by an attacker.
- Use Intrusion Detection Systems (IDS): Implement IDS solutions that detect and alert on suspicious ARP activity, such as unexpected ARP replies.
- Analyze Packets with Wireshark: Best for experienced users, capture and inspect network packets using Wireshark to identify fake ARP messages.
- Employ Specialized Tools: Use software such as arpwatch, XArp, or ArpON to constantly monitor ARP mappings and alert you to irregularities such as changes to ARP entries.
Prevention Techniques
Network administrators can implement several measures to defend against ARP spoofing attacks:
1. Set Static ARP Entries
Manually configure the ARP tables with static entries to prevent dynamic updates. However, this method is not scalable to large networks.
2. ARP Inspection
Use dynamic ARP inspection (DAI) on network switches to validate ARP packets. DAI helps ensure that only legitimate ARP requests and responses are processed.
3. Encryption
Encrypt sensitive data with protocols such as HTTPS, SSH, or VPN. Even if an attacker intercepts the traffic, encryption makes the data unreadable.
4. Network Segmentation
Divide the network into smaller segments to limit the potential impact of an ARP spoofing attack. This makes it more difficult for an attacker to compromise the entire network.
5. Regular Monitoring
Continuously monitor network traffic for signs of unusual ARP activity. Tools such as Wireshark and specialized network monitoring systems can alert administrators to suspicious behavior.
