🔍 Search
📥 Subscribe
Honeypot in Cyber Security
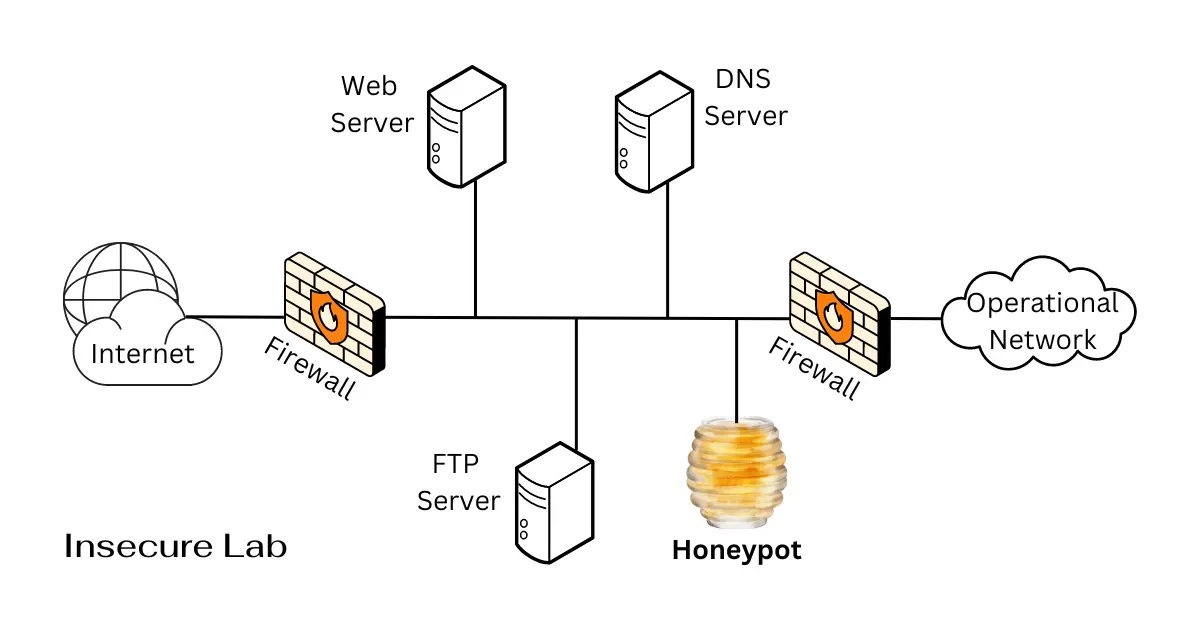
Table of Contents
This comprehensive guide explains the concept of honeypots in cyber security, their types, deployment strategies, benefits, and examples of honeypot software.
What is a Honeypot?
A honeypot is a security mechanism that simulates vulnerable systems, services, or networks to deceive attackers. It operates as a trap, enticing malicious actors to interact with it, thereby allowing security professionals to monitor, analyze, and respond to their activities.
The term "honeypot" comes from the idea of attracting and trapping malicious actors, much like bees are attracted to honey.
The primary purpose of a honeypot is to gather information about attackers' tactics, techniques, and procedures (TTPs), as well as to distract and divert them from legitimate systems and resources.
How does Honeypot Work?
Honeypots can be deployed in various ways, such as within a network to detect internal threats, on the internet to detect external threats, or even on specific systems or services to lure attackers away from critical resources.
When an attacker interacts with the honeypot, the system captures information about the attacker's methods, such as the IP address, tools and techniques used, and the specific actions taken. This information can then be used to improve security measures and better protect real systems and networks from future attacks.
Types of Honeypots
These can be classified based on two main factors:
- Deployment: This refers to where the honeypot is located on a network.
- Interaction Level: This describes the level of functionality and realism offered by the honeypot.
Based on Deployment:
1. Production honeypots
These are deployed in production environments and simulate real systems and services that an organization might use. These are often used to detect attacks against specific systems or services, such as web servers or email servers.
2. Research honeypots
These are designed to be used by researchers and security professionals to gather data about cyber attacks and attackers. These are often deployed in controlled environments and can be customized to simulate a wide variety of systems and services.
Based on Interaction Level:
1. High-interaction honeypots
These completely simulate real systems and services, giving attackers the impression that they are interacting with a legitimate system. These are more difficult to set up and maintain, but they can provide more detailed information about attackers and their methods.
2. Low-interaction honeypots
These emulate only the most common protocols and services, such as HTTP or FTP. These are easier to set up and maintain, but provide less detailed information about the attackers.
3. Pure honeypots
This type is designed to be completely passive, meaning it does not interact with attackers in any way. It is a decoy system or network set up to attract and detect attacks, without taking any active measures to prevent or respond to the attacks.
Honeypot Softwares
Here are some examples of popular honeypot software:
• Honeyd
Honeyd is a low-interaction honeypot that simulates a variety of different systems and services. It is easy to set up and is often used for research and education purposes.
• Glastopf
Glastopf is a web application honeypot that can detect a variety of web application attacks, such as SQL injection and cross-site scripting (XSS). It is written in Python and can be easily deployed on a variety of platforms.
• Dionaea
Dionaea is a high-interaction honeypot that is designed to capture malware samples and gather information about attackers. It supports a wide range of protocols and services, including HTTP, FTP, SMB, and VoIP.
• Cowrie
Cowrie is an SSH honeypot that can mimic a vulnerable SSH server. It can be used to capture attacker keystrokes and commands, and it can also be used to honeynet attackers, which is the practice of deploying multiple honeypots to waste an attacker's time and resources.
• Kippo
Kippo is a high-interaction honeypot that emulates an SSH server. It captures information about attackers, including their usernames, passwords, and commands used.
Summary
Honeypots are a valuable tool for organizations of all sizes looking to strengthen their cybersecurity posture. By understanding their capabilities and limitations, security teams can leverage honeypots to gain valuable insights into attacker behavior, identify vulnerabilities, and proactively defend their systems. Remember, honeypots are most effective when used as part of a layered security strategy that includes firewalls, intrusion detection systems, and other security controls.
